easyRSA
信息加密与验证
How can you ensure that the person receiving your message knows that you wrote it?
You’ve been asked out on a date, and you want to send a message telling them that you’d love to go, however a jealous lover isn’t so happy about this.
When you send your message saying yes, your jealous lover intercepts the message and corrupts it so it now says no!
We can protect against these attacks by signing the message.
Imagine you write a message M. You encrypt this message with your friend’s public key: C = Me0 mod N0.
To sign this message, you calculate the hash of the message: H(M) and “encrypt” this with your private key: S = H(M)d1 mod N1.
Your friend can decrypt the message using their private key: m = Cd0 mod N0. Using your public key they calculate s = Se1 mod N1.
Now by computing H(m) and comparing it to s: assert H(m) == s, they can ensure that the message you sent them, is the message that they received!
In real cryptosystems, it’s best practice to use separate keys for encrypting and signing messages.
大意就是给了一个消息,对其用朋友的公钥加密,让朋友用朋友的私钥解密获得原消息
同时,对消息的HASH值用自己的私钥加密,让朋友用自己的公钥解密,并与获得的消息的HASH值比对
如果HASH值相同,那就说明消息并没有被篡改
1 | ooo = bytes_to_long(hashlib.sha256(flag).digest()) |
由于HASH加密后的值无法进行计算,所以我们需要先用.digest()将其转换成bytes形式,再将bytes转化成可以计算的Long整型值。
查看n的素因子
遇到了一个N, 可以先去factordb.com查看一下N的素因子是否曾被记录,若可被完全分解,知道了p和q,那么问题就迎刃而解了
小公钥指数攻击:
e=1
由于gmpy2.invert(1, k)对于任意的 K, 得到的结果都为 1
则我们可以直接print(long_to_bytes(pow(c, 1, n)))得到结果
e很小,且c 远远小于 n
即说明 flag ** e = c, 可推出结果
低解密指数攻击:
Wiener’s Attack
在RSA中d也称为解密指数,当d比较小的时候,e也就显得特别大了。
适用情况:e过大或过小(一般e过大时使用)
可以使用附件RSA工具里的rsa-wiener-attack-master
在 d 比较小(d < 1/3 * N ** 1 / 4)时,攻击者可以使用 Wiener’s Attack 来获得私钥。
Boneh attack
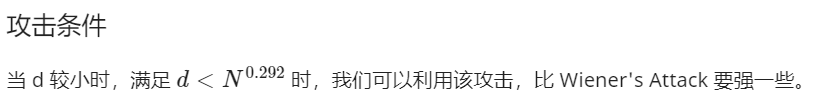
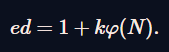
由于公钥e的选取和 φ(N)的大小差不多,所以k的大小和d的大小差不多,于是有
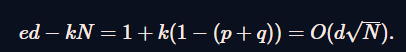
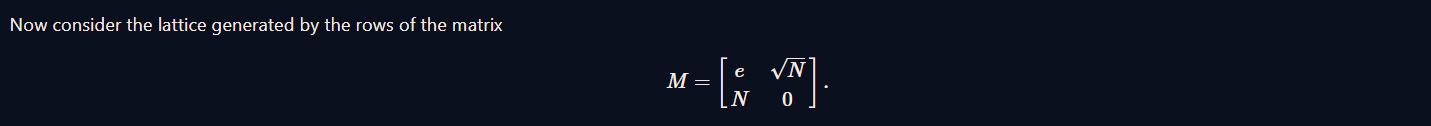
Then the vector 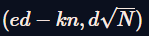 is a short vector of the lattice, under the assumption that d is very low. Applying a lattice reduction (see the CryptoHack challenge Gaussian Reduction to implement it yourself, or use LLL), this vector can be found, and d can be extracted from its second coordinate.
is a short vector of the lattice, under the assumption that d is very low. Applying a lattice reduction (see the CryptoHack challenge Gaussian Reduction to implement it yourself, or use LLL), this vector can be found, and d can be extracted from its second coordinate.
下面是使用 SageMath version 9.1的题解
1 | N = 0x665166804cd78e8197073f65f58bca14e019982245fcc7cad74535e948a4e0258b2e919bf3720968a00e5240c5e1d6b8831d8fec300d969fccec6cce11dde826d3fbe0837194f2dc64194c78379440671563c6c75267f0286d779e6d91d3e9037c642a860a894d8c45b7ed564d341501cedf260d3019234f2964ccc6c56b6de8a4f66667e9672a03f6c29d95100cdf5cb363d66f2131823a953621680300ab3a2eb51c12999b6d4249dde499055584925399f3a8c7a4a5a21f095878e80bbc772f785d2cbf70a87c6b854eb566e1e1beb7d4ac6eb46023b3dc7fdf34529a40f5fc5797f9c15c54ed4cb018c072168e9c30ca3602e00ea4047d2e5686c6eb37b9 |





